Dynamic Device Scope Tags with Azure Automation
It feels like eventually all customers end up in this situation where they need to tag devices for administration, invoicing or something else. So the purpose of this post is to help you automate this process with the help of a PowerShell runbook in azure automation.
Updated 2021–10–10 — Thanks to Michael Mardahl for pointing out that managed identity should be used instead of client secrets.
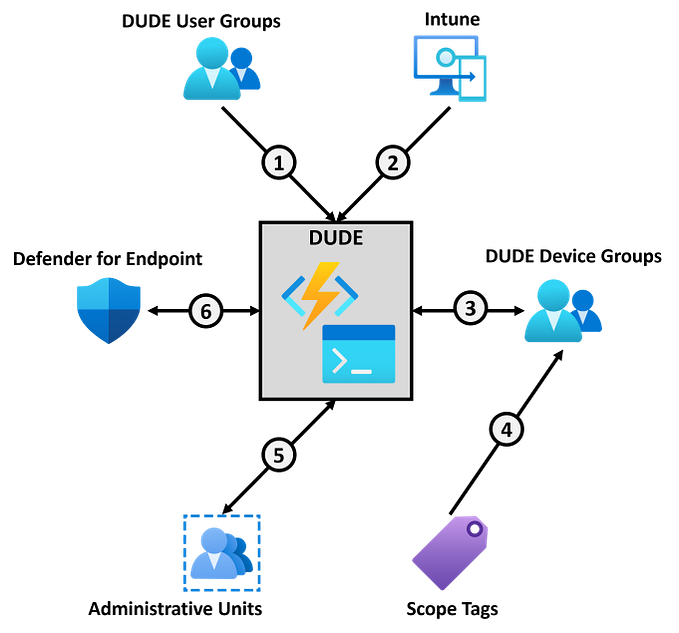
I will explain how you could set this up by creating dynamic user groups, for example for the HR department, and then have the Runbook gather all the HR users devices from Intune and add them to the correct device group automatically. If the user attribute changes, for example if a user leaves the HR department, their devices will be removed from the device group automatically.
Note that it’s critical that the user and device group names are consistent and have a matching ending. The first part of the group names will need to be defined in the script as the $UserGroupNames and $DeviceGroupNames variables.
If you enter the following custom variables:
- $UserGroupNames = “Endpoint-DUDE Users”
- $DeviceGroupNames = “Endpoint-DUDE Devices”
All your user group names should start with “Endpoint-DUDE Users” and all your device group names should start with “Endpoint-DUDE Devices”. Whatever you choose to put after this in the group names have to match between the two.
Example
User Group Names:
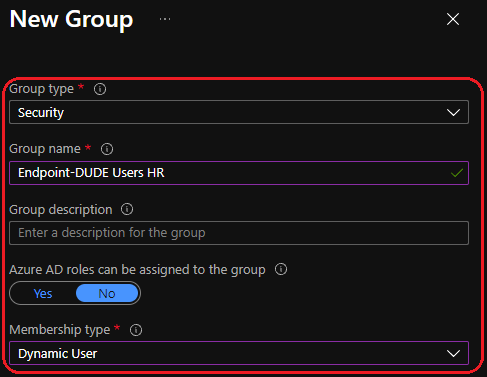
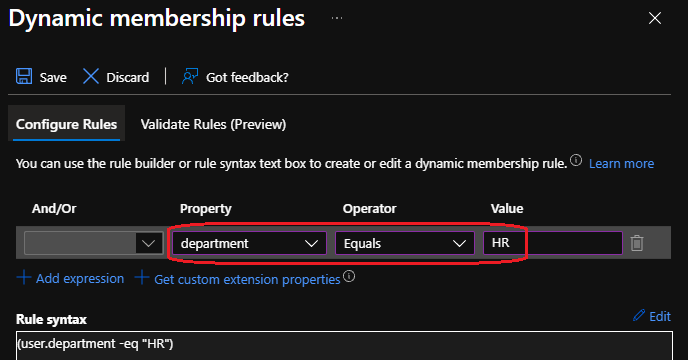
- Endpoint-DUDE Users HR
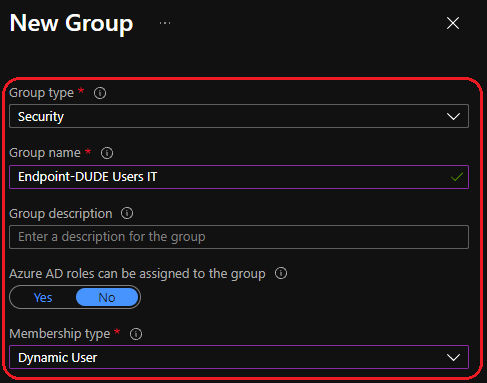
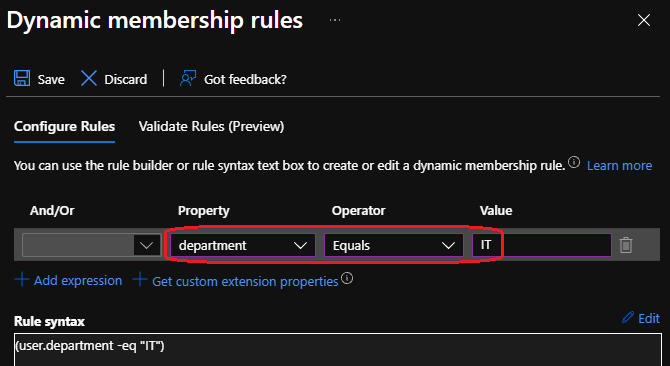
- Endpoint-DUDE Users IT
- Endpoint-DUDE Users Sweden
- Endpoint-DUDE Users North Europe
Device Group Names:
- Endpoint-DUDE Devices HR
- Endpoint-DUDE Devices IT
- Endpoint-DUDE Devices Sweden
- Endpoint-DUDE Devices North Europe
Let’s dig in…
User & Device Groups
To make this as dynamic as possible we would want to create dynamic user groups based on a user attribute. In this example I will create two dynamic user groups based on the departments “HR” and “IT”. DUDE in the group names stands for Dynamic User and Device Enumeration. Head over to Groups — Microsoft Azure to create our groups.
User group 1 — HR
User group 2 — IT
For each dynamic user group we need to create the corresponding device group. The device groups will have the assigned membership type so that our Runbook can add and remove devices.
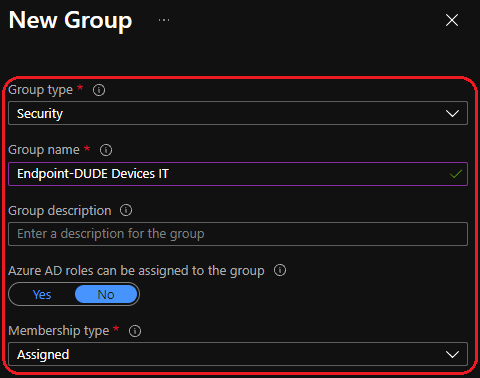
Device group 1 — HR
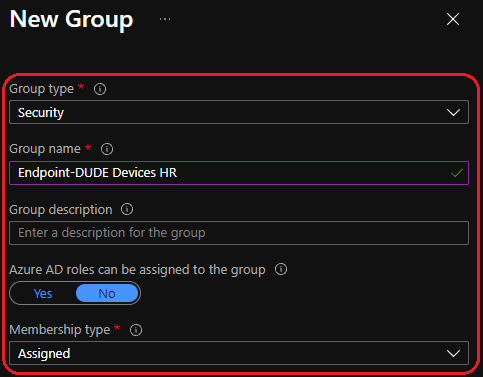
Device group 2 — IT
Scope Tags
Head over to Endpoint Manager roles — Microsoft Endpoint Manager admin center to create scope tags for our newly created device groups.
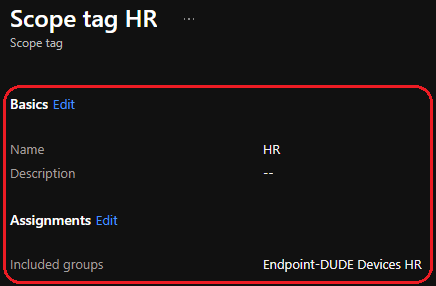
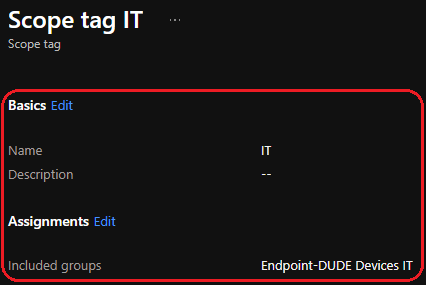
Automation Account
We need to create a automation account that will be running the runbook. Head over to Automation Accounts — Microsoft Azure , click “create” and fill the required information and click “create” again.
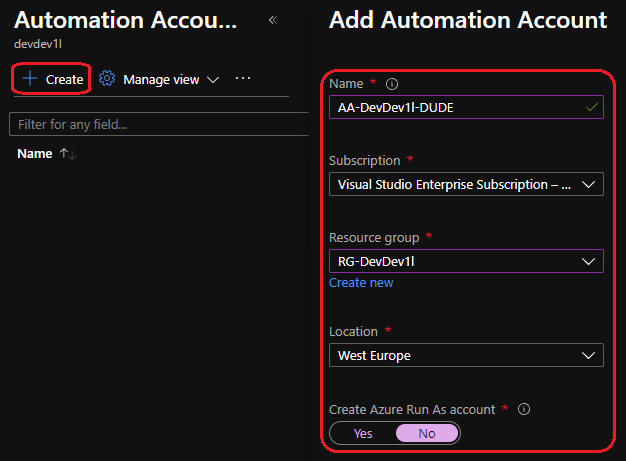
Let’s add the Microsoft.Graph.Authentication module. Open the newly created automation account and click “modules gallery” and search for “Microsoft.Graph.Authentication”
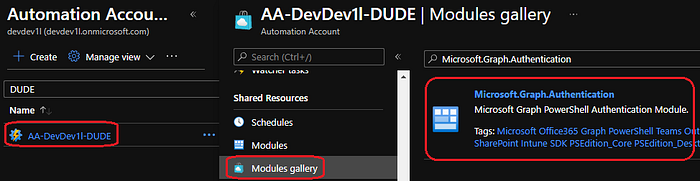
Click “import” and click “OK”
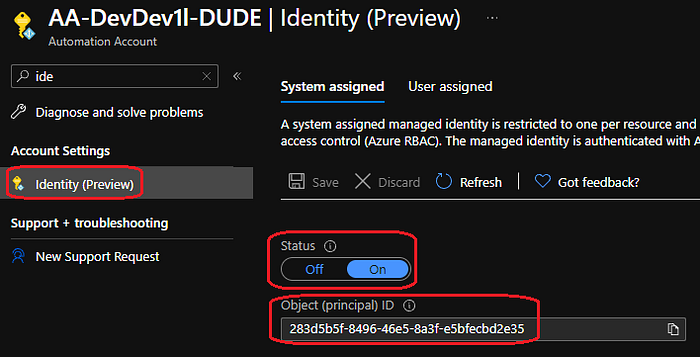
We will use a managed identity to access our resources securely, for more information about managed identities in azure automation please check out this great post by Michael Mardahl. On your automation account, select “identity”, turn on system assigned managed identity and make a note of the “object (principal) ID”
We need to add the permissions needed via PowerShell. Install the AzureAD module if you don’t already have (Install-Module AzureAD). Make sure to update the $TenantID and $PrincipalID variables before executing
# Variables
$TenantID = ".onmicrosoft.com"
$PrincipalID = "283d5b5f-8496-46e5-8a3f-e5bfecbd2e35"
# Add permissions
$Permissions = "Device.Read.All", "DeviceManagementManagedDevices.Read.All", "Group.Read.All", "GroupMember.ReadWrite.All", "User.Read.All"
Connect-AzureAD -TenantId $TenantID
$GraphServicePrincipal = Get-AzureADServicePrincipal -SearchString "Microsoft Graph" | Select-Object -first 1
$AppRole = $GraphServicePrincipal.AppRoles | Where-Object { $Permissions -contains $_.Value -and $_.AllowedMemberTypes -contains "Application" }
foreach ($Role in $AppRole) {
New-AzureAdServiceAppRoleAssignment -ObjectId $PrincipalID -PrincipalId $PrincipalID -ResourceId $GraphServicePrincipal.ObjectId -Id $Role.Id
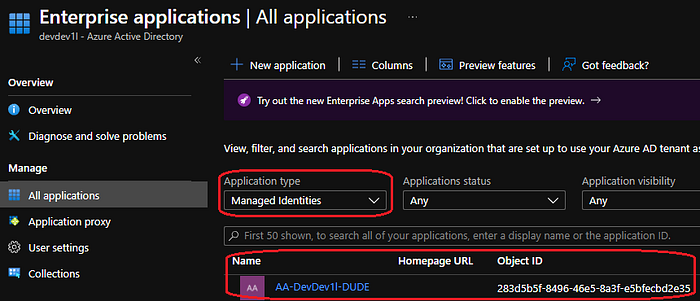
}Head over to Enterprise applications — Microsoft Azure to verify the permissions. Select “managed identities” as the application type and open your system assigned managed identity. The object ID value matches the object ID of the managed identity that you previously created.
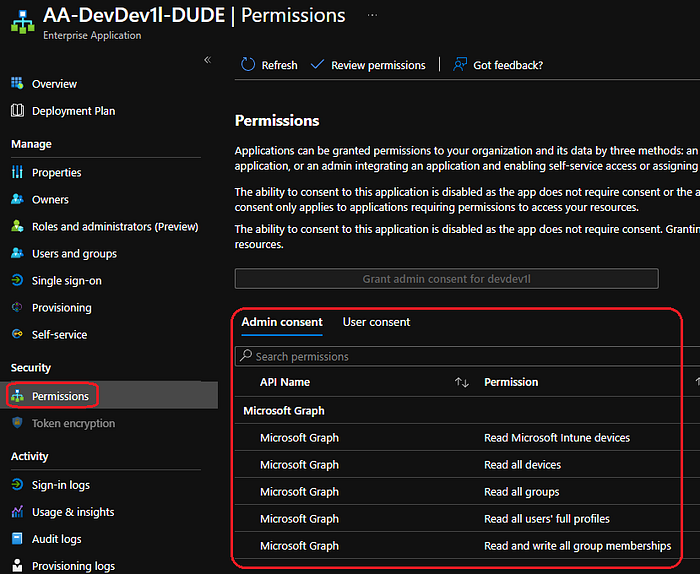
Select “permissions” and it should look something like this:
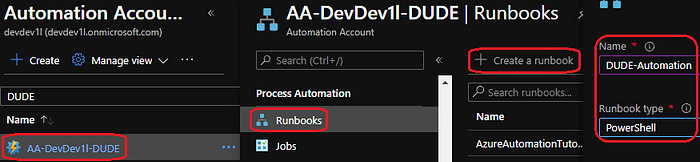
Runbook
We are now ready to create our runbook. Go to Automation Accounts — Microsoft Azure and select the automation account again, click “runbooks”, click “create a runbook” and enter a “name” and select PowerShell as the “runbook type” and click “create”
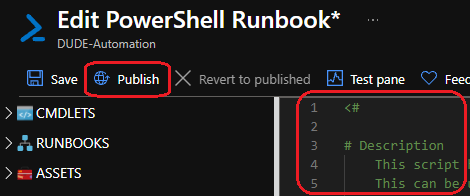
Download the PowerShell script from my GitHub > Intune/DUDE-AzureAutomation.ps1 at main · danielmoonpetri/Intune (github.com)
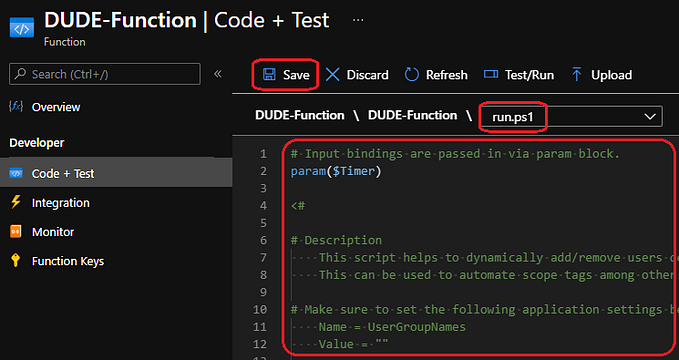
Don’t forget to edit the custom variables in the script with your user and device group names.
# Custom Variables
$UserGroupNames = ""
$DeviceGroupNames = ""Paste the updated script and hit “publish”
Click on “schedules” and select “add a schedule” to add the desired schedule. I recommend running this once or twice a day.
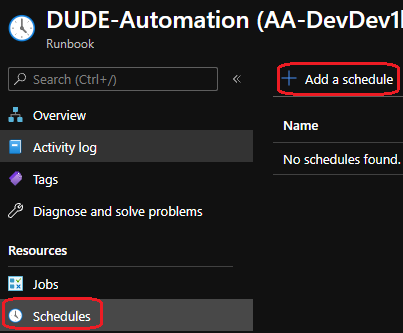
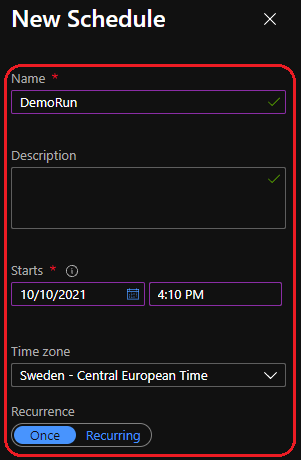
For demo purpose I will set this to run once
Results
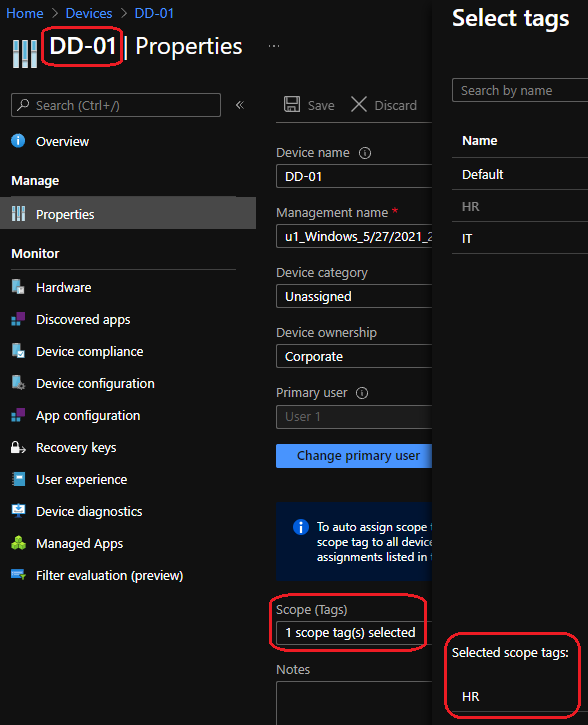
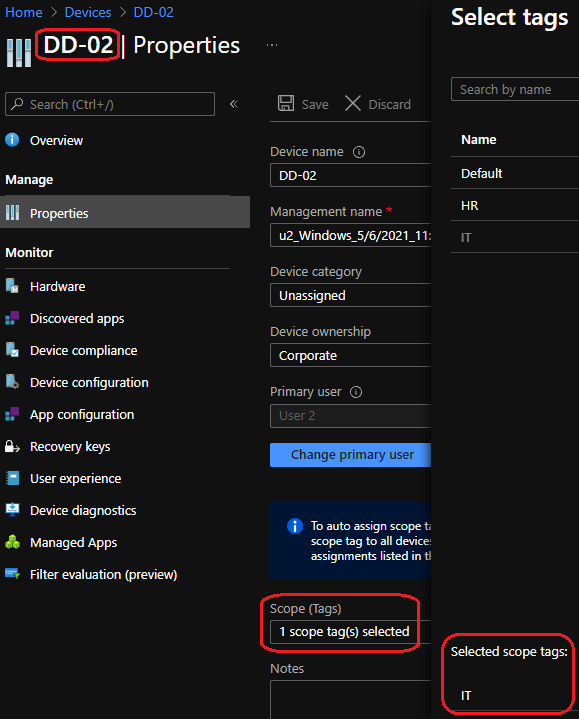
After the runbook have executed according to our schedule we can see the following results:
Device group members
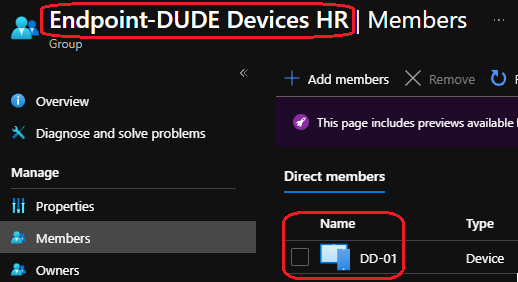
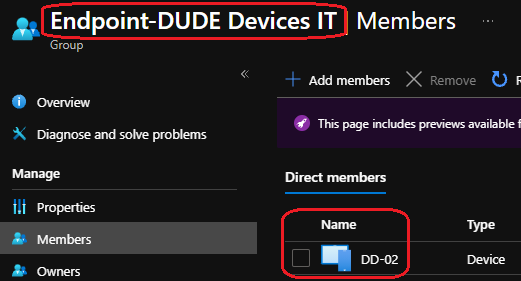
Device Scope Tags
Logging
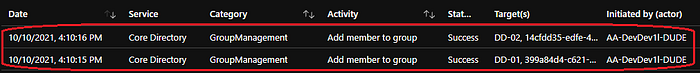
All actions will be logged in the audit logs
If we check the completed jobs output of the runbook we will get something like this:
Loading Custom Variables...
Custom Variables loaded
Loading Global Variables...
Global Variables loaded
Retrieving AccessToken...
AccessToken retrieved
Loading AllManagedDevices...
Found 9 AllManagedDevices
Loading AllUserGroups...
Found 2 AllUserGroups
Loading AllDeviceGroups...
Found 2 AllDeviceGroups
Running group Endpoint-DUDE Users HR (Group 1 of 2)...
Loading UserGroupMembers...
Found 1 UserGroupMembers
Loading UserGroupMembersDevices...
Found 1 UserGroupMembersDevices
Loading matching DeviceGroup...
Matching device group is Endpoint-DUDE Devices HR
Loading DeviceGroupMembers...
Found 0 DeviceGroupMembers
Loading DevicesToAdd...
Found 1 DevicesToAdd
Loading DevicesToRemove...
Found 0 DevicesToRemove
Running device DD-01 (Device 1 of 1 to add)...
Trying to add the device...
Device added successfully
Running group Endpoint-DUDE Users IT (Group 2 of 2)...
Loading UserGroupMembers...
Found 1 UserGroupMembers
Loading UserGroupMembersDevices...
Found 1 UserGroupMembersDevices
Loading matching DeviceGroup...
Matching device group is Endpoint-DUDE Devices IT
Loading DeviceGroupMembers...
Found 0 DeviceGroupMembers
Loading DevicesToAdd...
Found 1 DevicesToAdd
Loading DevicesToRemove...
Found 0 DevicesToRemove
Running device DD-02 (Device 1 of 1 to add)...
Trying to add the device...
Device added successfullyThe End
That’s it! We have now automated the device group assignments based on dynamic user groups and added scope tags. All we have to do now is to add more dynamic user groups, empty device group, assign scope tags and the runbook will take care of the rest.
Enjoy!